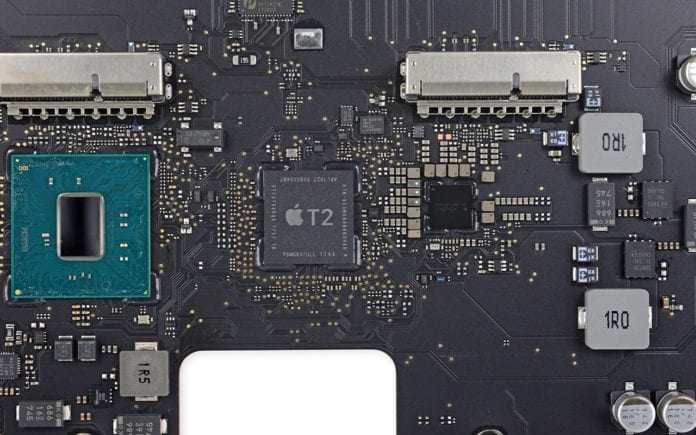
The current generation of Macs and MacBooks runs on the intel chipsets, along with the T2 chip which is a security-oriented co-processor that provides hardware-level security. Apart from security benefits, it also serves a bunch of other purposes like streaming 4K DRM protected content, physically disconnecting the mic after closing the lid of Mac. But, the irony is that this security chip isn’t secure anymore as security researcher Niels Hofmans has found a security flaw that can be used to hack Mac.
According to Niels Hofmans, the T2 security chip is based on the Apple’s A10 Bionic processor which was vulnerable to the checkm8 exploit that was used to jailbreak iPhones. Apple’s T2 chip is, similarly, vulnerable to the same exploit which can be used to hack the T2 chip.
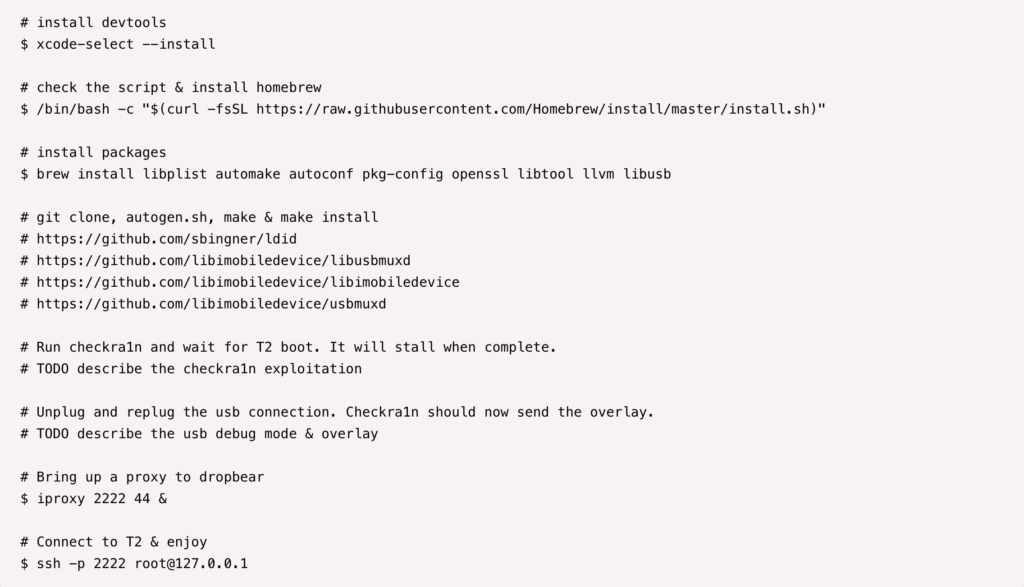
Well, the checkm8 exploit is not alone capable to bypass T2’s security protocols as the laptop enters into Device Firmware Update (DFU) mode as soon T2 chip detects some abnormality and restores the software and the firmware of the device with a fatal error. But, the T2 chip is also vulnerable to another exploit known as BlackBird that can be used along with checkm8 exploit to bypass the check and gain complete access of the system.
Also Read: Apple Confirms ARM Chips for Mac – WWDC 2020
Once an attacker has access to the T2 chip, they will have complete root access and kernel execution privileges, which, basically, means the attacker will gain complete control of your Mac but the files encrypted using FileVault 2 will be safe at first but attackers can use a keylogger to steal passwords since the T2 chip is responsible for the keyboard access.
Hoffman also claims that this method can be also used to bypass Apple’s Find My Device which means you won’t be able to even lock your Apple device remotely if it gets misplaced or stolen and a firmware password won’t help because it requires keyboard access which is managed by the T2 chip itself.
This exploit is not patchable that means Apple won’t be able to rectify this with any future software upgrade if somehow your computer gets attacked then you will have to reinstall bridgeOS on your T2 chip using Apple Configurator.
The attacker needs a hardware connection with the Mac which can be done using some malicious or specially-crafted USB-C cable.
How does it affect your Mac?
Well, you can’t just leave your Mac opened or even closed (this should be done in general) anywhere because any Mac or MacBook left unattended could be hacked by someone who can just connect a USB-C cable, reboot it, and then run Checkra1n 0.11.0.
This also opens doors for authorities for new investigation tools that could provide access to suspects’ Macs and MacBooks to retrieve needed information that would have not been possible in normal cases.
What can you do to protect your Mac or MacBook?
Well, the only way to exploit the T2 chip as of now is through any hardware connection so the best you can do is to keep an eye and just don’t insert any unverified USB-C device.
Niel Hoffman says that he tried to contact Apple multiple times but he never heard back from them and at last, he tried to inform Apple’s CEO, Tim Cook, about this exploit but he never got any reply from him. He suggests that Apple has no plans to accept this issue publicly which made him reveal this to the masses.
Hoffman also says that his sources have suggested that much more bad news is on its way and he quoted “Be afraid, be very afraid“.
You can read the full report on ironPeak services.