If your phone is operating below Android version 9.0 you might want to continue reading. Security researchers have found out a severe vulnerability that poses risks to users of Android versions below 9.0. This Android bug lets malware exploit and gain access to almost all applications.
This bug attacks a device by showing a fake interface which will trick users to give away sensitive information that includes drawing off app passwords, photos, contacts, track the real-time location of that device, make and keep records of phone calls, and also spy on the victims through camera and microphone.
Google has called this vulnerability as a ‘critical severity’ issue (CVE-2020-0096). According to Norwegian security firm Promon, which is primarily responsible for conducting the research, this is the “evil twin” to the bug with a similar name. StrandHogg 2.0 was revealed six months after the StrandHogg bug was originally discovered.
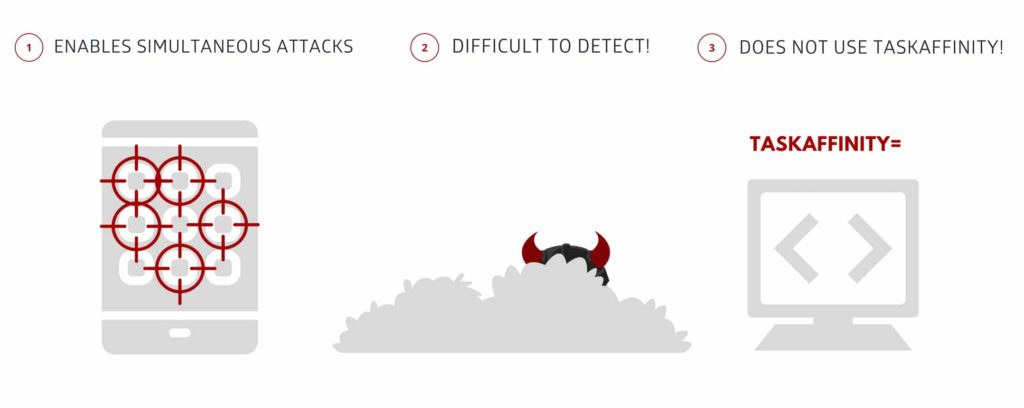
What makes it even worse is that this bug is “nearly undetectable” making it almost impossible for anti-virus and application security scanners to detect it in the first place. This is a reason why this version of StrandHogg is a lot more threatening than its predecessor, making users susceptible to broader attacks.
Promon mentioned that Google was informed about StrandHogg 2.0’s predecessor back in December 2019, allowing Google to come up with a patch for the bug. Google, however, has provided a patch to the Android ecosystem partners in April 2020 and for devices operating on Android 8.0, 8.1, and 9.0. Despite the update being rolled out, many OEMs do not always release these updates to keep the devices up to date, proving to be a risk to users.
There’s a bit of a relief, however, as Promon has decided to delay revealing the details of this bug because releasing it before Google comes up with a concrete solution to this “critical” vulnerability would simply be hazardous.
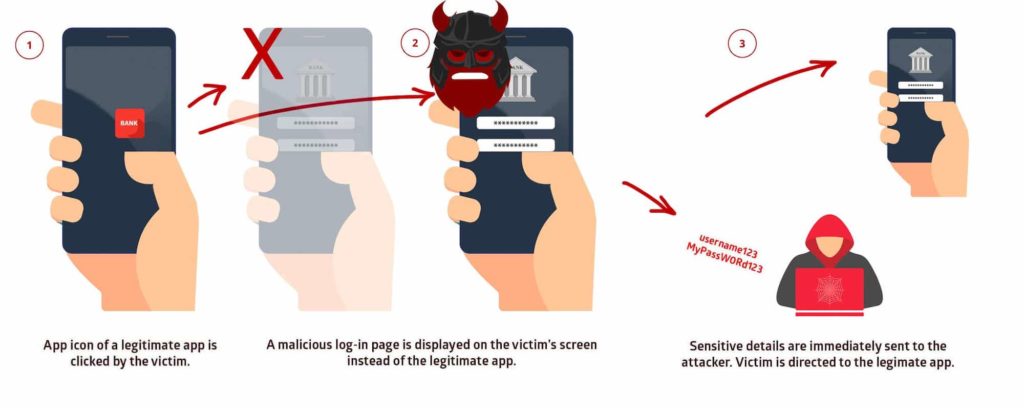
So how does this bug work?
A user taps on an app icon of a particular app which proves to be a malicious app in the guise of a legitimate one. The bug will then intercept and gain access to sensitive information by showing a false login window for the app. Once the password and other sensitive information, such as online banking credentials, are fed into the malicious app, the hacker’s server receives the information. StrandHogg 2.0’s predecessor could attack one app at a time, StrandHogg 2.0 can access almost every app simultaneously.
To compound problems, StrandHogg 2.0 doesn’t require Android permissions to run, it can assume the identity to quickly give permissions to hijack and gain access to contacts, photos and much more. Two-factor authentication also cannot defeat StrandHogg 2.0. A spokesperson for Google has mentioned that they have released the fix for the issue identified by Promon. An app screening service will block the apps trying to exploit the StrandHogg 2.0 vulnerability.
How can you stay alert?
There is no guaranteed and dependable way that ensures that one can block the StrandHogg attacks. However, there are certain points that one can keep in mind while using the applications on their phones:
- Beware if an app that you are already logged in is asking for your login credentials again.
- If apps that do not ask for permissions at the first place are asking for permissions, there could be a possible attack.
- Check if a permission popup is suspiciously not displaying the name of that particular app.
- Look out for buttons and links in the user interface which are non-functional.
- Check if the back button is working as it is supposed to.
Along with keeping these points in mind, it is advised that Android users keep their devices updated as soon as they can.


